
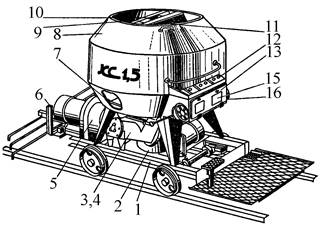
Кормораздатчик мобильный электрифицированный: схема и процесс работы устройства...
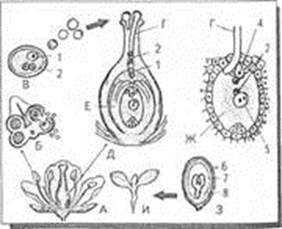
Двойное оплодотворение у цветковых растений: Оплодотворение - это процесс слияния мужской и женской половых клеток с образованием зиготы...

Кормораздатчик мобильный электрифицированный: схема и процесс работы устройства...

Двойное оплодотворение у цветковых растений: Оплодотворение - это процесс слияния мужской и женской половых клеток с образованием зиготы...
Топ:
Проблема типологии научных революций: Глобальные научные революции и типы научной рациональности...
Теоретическая значимость работы: Описание теоретической значимости (ценности) результатов исследования должно присутствовать во введении...
Генеалогическое древо Султанов Османской империи: Османские правители, вначале, будучи еще бейлербеями Анатолии, женились на дочерях византийских императоров...
Интересное:
Средства для ингаляционного наркоза: Наркоз наступает в результате вдыхания (ингаляции) средств, которое осуществляют или с помощью маски...
Подходы к решению темы фильма: Существует три основных типа исторического фильма, имеющих между собой много общего...
Как мы говорим и как мы слушаем: общение можно сравнить с огромным зонтиком, под которым скрыто все...
Дисциплины:
|
из
5.00
|
Заказать работу |
Содержание книги
Поиск на нашем сайте
|
|
|
|
1. A computer virus is a computer program that can copy itself and infect a computer without the permission or knowledge of the user. The term "virus" is also commonly but erroneously used to refer to other types of malware, adware and spyware programs that do not have the reproductive ability.
2. Malware comes from the words malicious and software, is software designed to infiltrate or damage a computer system without the owner's informed consent. Software is considered malware based on the perceived intent of the creator rather than any particular features. Malware is not the same as defective software, that is, software which has a legitimate purpose but contains harmful bugs.
3. Adware or advertising-supported software is any software program which automatically plays, displays, or downloads advertisements to a computer after the software is installed on it or while the application is being used.
4. Spyware is computer software that is installed surreptitiously on a personal computer to intercept or take partial control over the user's interaction with the computer, without the user's informed consent.
5. Spyware programs can collect various types of personal information, such as Internet surfing habits, sites that have been visited, but can also interfere with user control of the computer in other ways, such as installing additional software.
6. A true virus can only spread from one computer to another when its host is taken to the target computer, for instance because a user sent it over a network or the Internet, or carried it on a removable medium such as a floppy disk, CD, or USB drive. Viruses can increase their chances of spreading to other computers by infecting files on a network file system or a file system that is accessed by another computer.
7. Viruses are sometimes confused with computer worms and Trojan horses, which are technically different. A worm can spread itself to other computers without needing to be transferred as part of a host, and a Trojan horse is a program that appears harmless but has a hidden agenda. Worms and Trojans, like viruses, may cause harm to either a computer system's hosted data, functional performance, or networking throughput, when they are executed. Some viruses and other malware have symptoms noticeable to the computer user, but most are surreptitious. This makes it hard for the average user to notice, find and disable and is why specialist anti-virus programs are now commonplace.
8. In order to avoid detection by users, some viruses employ different kinds of deception. Some old viruses, especially on the MS-DOS platform, make sure that the "last modified" date of a host file stays the same when the file is infected by the virus.
9. Some viruses can infect files without increasing their sizes or damaging the files. They accomplish this by overwriting unused areas of executable files. Some viruses try to avoid detection by killing the tasks associated with antivirus software before it can detect them.
Ex. 3 Find in the text where it is said about the points given below. Put down the number of the paragraph
1. Program which automatically displays advertisement to a computer.
2. Computer program that infect a computer
3. Programs which can collect various types of personal information
4. Computer worms and Trojan horses
Ex. 4 Find the synonyms to the following words in the text:
1 to keep away (6)
2 to harm(5)
3 various (4)
4 instruction (1)
5 spread (5)
6 warms(2)
7 move (2)
Ex. 5 Find the terms in the text which describe the following. Put down the number of the paragraph :
a. to affect a large area or a bigger group of people
b. the international system of computer that makes it possible for a person
to see the information from the world
c. instruction that are put into computer program in order to stop it working
d. a collection of information on one subject that is stored together in a computer or one disk
e. a place where sth. comes from or where sth. is obtained
|
|
|
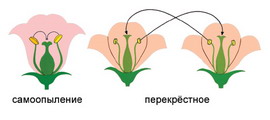
Семя – орган полового размножения и расселения растений: наружи у семян имеется плотный покров – кожура...

Историки об Елизавете Петровне: Елизавета попала между двумя встречными культурными течениями, воспитывалась среди новых европейских веяний и преданий...

Двойное оплодотворение у цветковых растений: Оплодотворение - это процесс слияния мужской и женской половых клеток с образованием зиготы...
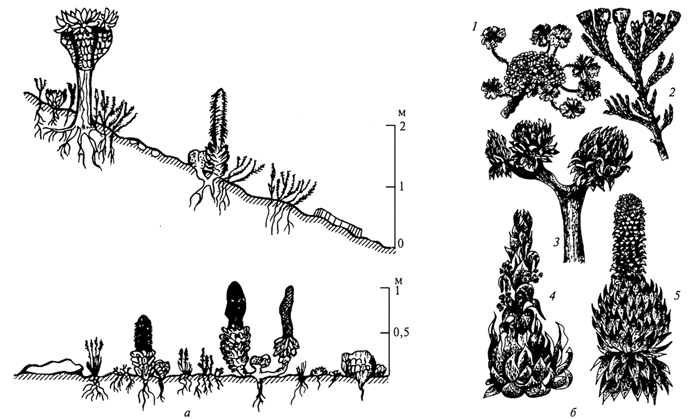
Адаптации растений и животных к жизни в горах: Большое значение для жизни организмов в горах имеют степень расчленения, крутизна и экспозиционные различия склонов...
© cyberpedia.su 2017-2026 - Не является автором материалов. Исключительное право сохранено за автором текста.
Если вы не хотите, чтобы данный материал был у нас на сайте, перейдите по ссылке: Нарушение авторских прав. Мы поможем в написании вашей работы!