
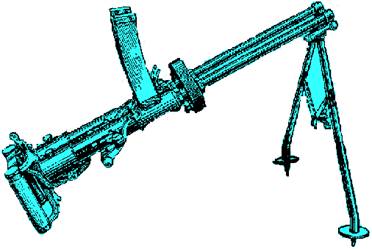
История развития пистолетов-пулеметов: Предпосылкой для возникновения пистолетов-пулеметов послужила давняя тенденция тяготения винтовок...
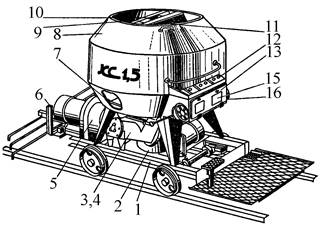
Кормораздатчик мобильный электрифицированный: схема и процесс работы устройства...

История развития пистолетов-пулеметов: Предпосылкой для возникновения пистолетов-пулеметов послужила давняя тенденция тяготения винтовок...

Кормораздатчик мобильный электрифицированный: схема и процесс работы устройства...
Топ:
Когда производится ограждение поезда, остановившегося на перегоне: Во всех случаях немедленно должно быть ограждено место препятствия для движения поездов на смежном пути двухпутного...
Установка замедленного коксования: Чем выше температура и ниже давление, тем место разрыва углеродной цепи всё больше смещается к её концу и значительно возрастает...
Интересное:
Инженерная защита территорий, зданий и сооружений от опасных геологических процессов: Изучение оползневых явлений, оценка устойчивости склонов и проектирование противооползневых сооружений — актуальнейшие задачи, стоящие перед отечественными...
Что нужно делать при лейкемии: Прежде всего, необходимо выяснить, не страдаете ли вы каким-либо душевным недугом...
Влияние предпринимательской среды на эффективное функционирование предприятия: Предпринимательская среда – это совокупность внешних и внутренних факторов, оказывающих влияние на функционирование фирмы...
Дисциплины:
|
из
5.00
|
Заказать работу |
|
|
|
|
Тексты для перевода
1 вариант
Computer viruses
Computer viruses are mysterious and grab our attention. On the one hand, viruses show us how vulnerable we are. A properly engineered virus can have an amazing effect on the worldwide Internet. On the other hand, they show how sophisticated and interconnected human beings have become.
For example, the things making big news right now are the MSBlaster worm and the SoBig virus. The Melissa virus -- which became a global phenomenon in March 1999 -- was so powerful that it forced Microsoft and a number of other very large companies to completely turn off their e-mail systems until the virus could be contained. The ILOVEYOU virus in 2000 had a similarly devastating effect. That's pretty impressive when you consider that the Melissa and ILOVEYOU viruses are incredibly simple.
In this article, we will discuss viruses -- both "traditional" viruses and the newer e-mail viruses -- so that you can learn how they work and also understand how to protect yourself. Viruses in general are on the wane, but occasionally a person finds a new way to create one, and that's when they make the news.
Types of Infection
When you listen to the news, you hear about many different forms of electronic infection. The most common are:
•Viruses - A virus is a small piece of software that piggybacks on real programs. For example, a virus might attach itself to a program such as a spreadsheet program. Each time the spreadsheet program runs, the virus runs, too, and it has the chance to reproduce (by attaching to other programs) or wreak havoc.
•E-mail viruses - An e-mail virus moves around in e-mail messages, and usually replicates itself by automatically mailing itself to dozens of people in the victim's e-mail address book.
•Worms - A worm is a small piece of software that uses computer networks and security holes to replicate itself. A copy of the worm scans the network for another machine that has a specific security hole. It copies itself to the new machine using the security hole, and then starts replicating from there, as well.
•Trojan horses - A Trojan horse is simply a computer program. The program claims to do one thing (it may claim to be a game) but instead does damage when you run it (it may erase your hard disk). Trojan horses have no way to replicate automatically.
2 вариант
Architecture (computer science)
Architecture (computer science), a general term referring to the structure of all or part of a computer system. The term also covers the design of system software, such as the operating system (the program that controls the computer), as well as referring to the combination of hardware and basic software that links the machines on a computer network. Computer architecture refers to an entire structure and to the details needed to make it functional. Thus, computer architecture covers computer systems, microprocessors, circuits, and system programs. Typically the term does not refer to application programs, such as spreadsheets or word processing, which are required to perform a task but not to make the system run.
|
|
Design elements
In designing a computer system, architects consider five major elements that make up the system's hardware: the arithmetic/logic unit, control unit, memory, input, and output. The arithmetic/logic unit performs arithmetic and compares numerical values. The control unit directs the operation of the computer by taking the user instructions and transforming them into electrical signals that the computer's circuitry can understand. The combination of the arithmetic/logic unit and the control unit is called the central processing unit (CPU). The memory stores instructions and data. The input and output sections allow the computer to receive and send data, respectively.
Different hardware architectures are required because of the specialized needs of systems and users. One user may need a system to display graphics extremely fast, while another system may have to be optimized for searching a database or conserving battery power in a laptop computer.
In addition to the hardware design, the architects must consider what software programs will operate the system. Software, such as programming languages and operating systems, makes the details of the hardware architecture invisible to the user. For example, computers that use the C programming language or a UNIX operating system may appear the same from the user's viewpoint, although they use different hardware architectures.
3 вариант
NETWORK ARCHITECTURE
Computers communicate with other computers via networks. The simplest network is a direct connection between two computers. However, computers can also be connected over large networks, allowing users to exchange data, communicate via electronic mail, and share resources such as printers.
Computers can be connected in several ways. In a ring configuration, data are transmitted along the ring and each computer in the ring examines this data to determine if it is the intended recipient. If the data are not intended for a particular computer, the computer passes the data to the next computer in the ring. This process is repeated until the data arrive at their intended destination. A ring network allows multiple messages to be carried simultaneously, but since each message is checked by each computer, data transmission is slowed.
In a bus configuration, computers are connected through a single set of wires, called a bus. One computer sends data to another by broadcasting the address of the receiver and the data over the bus. All the computers in the network look at the address simultaneously, and the intended recipient accepts the data. A bus network, unlike a ring network, allows data to be sent directly from one computer to another. However, only one computer at a time can transmit data. The others must wait to send their messages.
In a star configuration, computers are linked to a central computer called a hub. A computer sends the address of the receiver and the data to the hub, which then links the sending and receiving computers directly. A star network allows multiple messages to be sent simultaneously, but it is more costly because it uses an additional computer, the hub, to direct the data.
Recent advances
One problem in computer architecture is caused by the difference between the speed of the CPU and the speed at which memory supplies instructions and data. Modern CPUs can process instructions in 3 nanoseconds (3 billionths of a second). A typical memory access, however, takes 100 nanoseconds and each instruction may require multiple accesses. To compensate for this disparity, new computer chips have been designed that contain small memories, called caches, located near the CPU. Because of their proximity to the CPU and their small size, caches can supply instructions and data faster than normal memory. Cache memory stores the most frequently used instructions and data and can greatly increase efficiency.
|
|
Задания к текстам (одинаковы для всех вариантов)
|
|
|
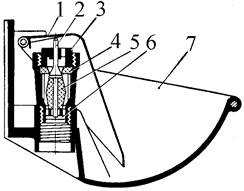
Индивидуальные и групповые автопоилки: для животных. Схемы и конструкции...
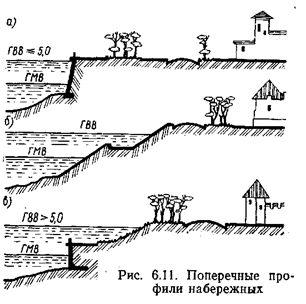
Поперечные профили набережных и береговой полосы: На городских территориях берегоукрепление проектируют с учетом технических и экономических требований, но особое значение придают эстетическим...
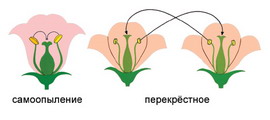
Семя – орган полового размножения и расселения растений: наружи у семян имеется плотный покров – кожура...

История развития пистолетов-пулеметов: Предпосылкой для возникновения пистолетов-пулеметов послужила давняя тенденция тяготения винтовок...
© cyberpedia.su 2017-2024 - Не является автором материалов. Исключительное право сохранено за автором текста.
Если вы не хотите, чтобы данный материал был у нас на сайте, перейдите по ссылке: Нарушение авторских прав. Мы поможем в написании вашей работы!