
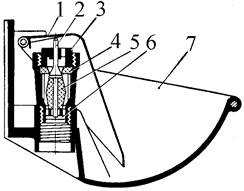
Индивидуальные и групповые автопоилки: для животных. Схемы и конструкции...
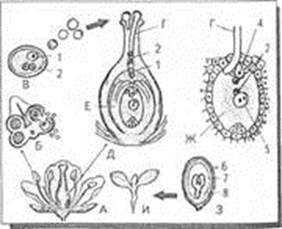
Двойное оплодотворение у цветковых растений: Оплодотворение - это процесс слияния мужской и женской половых клеток с образованием зиготы...

Индивидуальные и групповые автопоилки: для животных. Схемы и конструкции...

Двойное оплодотворение у цветковых растений: Оплодотворение - это процесс слияния мужской и женской половых клеток с образованием зиготы...
Топ:
Устройство и оснащение процедурного кабинета: Решающая роль в обеспечении правильного лечения пациентов отводится процедурной медсестре...
Методика измерений сопротивления растеканию тока анодного заземления: Анодный заземлитель (анод) – проводник, погруженный в электролитическую среду (грунт, раствор электролита) и подключенный к положительному...
Выпускная квалификационная работа: Основная часть ВКР, как правило, состоит из двух-трех глав, каждая из которых, в свою очередь...
Интересное:
Мероприятия для защиты от морозного пучения грунтов: Инженерная защита от морозного (криогенного) пучения грунтов необходима для легких малоэтажных зданий и других сооружений...
Что нужно делать при лейкемии: Прежде всего, необходимо выяснить, не страдаете ли вы каким-либо душевным недугом...
Аура как энергетическое поле: многослойную ауру человека можно представить себе подобным...
Дисциплины:
|
из
5.00
|
Заказать работу |
|
|
|
|
Упражнение 2. Translate the text.
Computer is one of the inventions of the 20th century.
Computer is one of the inventions of the 20th century that changed the world greatly. The first computers of the 1940th were enormous. But now they are almost in every family and in every office building. Some machines do only one job, some of them are multifunctional, but no device is as multifunctional as computer. The parts of the computer (or its hardware) remain the same, you change only the program (software) and your computer immediately learns to do various things. A browser program is designed to look at pages on the Internet (you can also say «to browse», this accounts for the word «browser»). A word processor program lets you print texts and then change styles of fonts and sizes of pages. A database program is used for searching and sorting records. Such programs are used at shops, libraries, hospitals, accountant offices and many other places. They make work with great amounts of data much quicker. Computers are found everywhere and used in every sphere of life. At a plant one can make a computer model of a car or plane and check its resistance to stress. Such calculations without a computer could have taken several months. Computer is also used at school: children watch presentations, films and web pages. This help them to study effectively. Computers also have some disadvantages. there is a famous joke that computers are designed to solve problems but half of the time they are the problem. As computer is a complicated device, one small breakage may stop its work. Moreover, the equipment is soon out of date. Besides, there is a problem of compatibility. First of all, there are hardware devices which can't work with the old operating system, such as a processor, a hard disk drive, a video card, etc. Then, there are programs which need more resources than computer actually has. Thirdly, computers become more and more complicated, and much effort is required to learn how to work with them. Fourthly, computer viruses cause a lot of trouble – they can spoil, remove or steal computer data, and every user knows it well from his personal experience. And on top of all, computer is a multifunctional device, as we already know, so it can be used both to do work and to entertain oneself. Children often fall prey to computer and Internet: they play computer games, spend their free time chatting with friends on the Internet and doing practically nothing. This aspect can't be denied. To crown it all, computer is a useful device like many others, designed to help people.
Раздел 4. Интернет.
Что такое Интернет?
Упражнение 1. Translate the text.
The Internet.
We can’t imagine our lives without the internet, computers and other gadgets, which unite all the users of World Wide Web. The internet is a very important source of information for people. Nowadays, you can find there any necessary information not only for education, or work but also for entertainment. Nowadays people communicate with each other, using the internet, social networks are very popular and people can’t imagine their lives without online communication.
|
|
But we must say, that using the internet has both advantages and disadvantages. The internet influences us very much, especially young people. There exist dozens of diseases that are the result of playing computer games, and spending too much time in networks. We do sport and walk less and less and spend time, sitting at a computer. Also, using a computer, there exist a possibility to become a victim of online fraudsters, which can try to steal your money.
Internet became so popular nowadays because people can use it not only at home, in the personal computer, but also they can go online, using their mobile web. So we can get any information we want, no matter, whether we are at home or not. And in addition, the price of such mobile web is not so expensive.
Услуги Интернета.
Упражнение 2. Translate the text.
The Internet. Part II.
The Internet, or the Net, as it is more often called in the English- speaking countries, is considered to be one of the most important inventions of the twentieth century. Some people say that it is like having thousands of consultants who are ready to answer any of your questions.
It is a cheap and reliable source of information — and not only that. You can also send documents all over the world, sample new music, visit museums all over the world, read books, exchange letters with your friends in another continent and receive their answer in a quarter of an hour, sell and buy things, play games, read the latest news and do a lot of other things.
But one shouldn't treat the Net as means of amusement when there is nothing else to do. In fact, the Internet has nowadays become a very important means of business correspondence, financial transactions, marketing, and much more. In fact, in the nearest future it will become as (or more) important as fax or telephone.
The Internet stands for international network of computers that are linked together to exchange information. The computers are joined through high-speed connections. To get on the Net, all you have to do is to connect your PC to any of these networked computers via an Internet Access Provider. The Net has capabilities for cheap, global and immediate communication. It may grow to dominate areas of publishing, news and education, banking and customer support.
What role does the Internet play today? There is no doubt it has greatly changed the way we live. Millions of people use it every day, whether they study, work or travel around the world.
As far as I am concerned, I can't imagine my life without the Internet. It helps me to get in touch with my friends who live abroad, to be abreast of the news in the world, to book tickets online, to purchase different goods at e-shops and to find all useful information like rare books, encyclopedias or dictionaries. I don't have to sit for hours in the libraries and rewrite all necessary information. Besides, the Internet helps me improve my language skills. I have a brilliant opportunity to practice English every day. To increase my fluency, I speak with my pen-pals from the USA through Skype.
Moreover, the Internet helps people widen the circle of acquaintances and friends. Many people visit chat rooms and have social network accounts. And finally the Internet helps schoolchildren with their school work. When it comes to writing reports, the Internet is the best assistant. Surfing the Internet, school children can find numerous sources of up-to-date information. However, the sources of information should be reliable. In my opinion, they must be restricted to those absolutely essential and helpful in studies, such as encyclopedias, electronic books and dictionaries.
However, many people believe that the Internet has a negative influence on people, especially younger generation, and, on the whole, on human interaction. So, should parents limit the time their children spend on the Internet? Well, with the invention of personal computer children do spend less time with their friends and often avoid face-to-face communication. Most of them would prefer to play online games or chat on the Internet rather than go out. Some children do not do their homework, miss classes and lag behind their schoolmates. Some of them become addicted to the computer and disobey their parents. In my opinion, in this case grown-ups should install any parental control program which will help them monitor the time spent on the Internet and protect them from viewing offensive pop-ups and inappropriate information. I would like to emphasize that children must distinctly apprehend that the main purpose of a computer is to educate, not to entertain.
|
|
So, how will the internet look like in the future? It is hard to predict, of course, but I think that in the nearest future lots of online schools and universities will appear. It will help people who live far away from big cities or disabled people to get education without leaving home.
Taking into consideration all mentioned above, I consider that the Internet promotes new acquaintances and relationships among social groups. All the same, people should try to maintain a balance between their real and virtual life.
Компьютерные вирусы.
Упражнение 3. Translate the text.
Computer viruses.
A virus is a piece of software designed and written to adversely affect your computer by altering the way it works without your knowledge or permission. In more technical terms, a virus is a segment of program code that implants itself to one of your executable files and spreads systematically from one file to another. Computer viruses do not spontaneously generate: They must be written and have a specific purpose. Usually a virus has two distinct functions:
Spreads itself from one file to another without your input or knowledge. Technically, this is known as self-replication and propagation.
Implements the symptom or damage planned by the perpetrator. This could include erasing a disk, corrupting your programs or just creating havoc on your computer. Technically, this is known as the virus payload, which can be benign or malignant at the whim of the virus creator. A benign virus is one that is designed to do no real damage to your computer. For example, a virus that conceals itself until some predetermined date or time and then does nothing more than display some sort of message is considered benign.
A malignant virus is one that attempts to inflict malicious damage to your computer, although the damage may not be intentional. There are a significant number of viruses that cause damage due to poor programming and outright bugs in the viral code. A malicious virus might alter one or more of your programs so that it does not work, as it should. The infected program might terminate abnormally, write incorrect information into your documents. Or, the virus might alter the directory information on one of your system area. This might prevent the partition from mounting, or you might not be able to launch one or more programs, or programs might not be able to locate the documents you want to open.
Some of the viruses identified are benign; however, a high percentage of them are very malignant. Some of the more malignant viruses will erase your entire hard disk, or delete files.
|
|
What Viruses Do
Some viruses are programmed specifically to damage the data on your computer by corrupting programs, deleting files, or erasing your entire hard disk. Many of the currently known Macintosh viruses are not designed to do any damage. However, because of bugs (programming errors) within the virus, an infected system may behave erratically.
What Viruses Don't Do
Computer viruses don't infect files on write-protected disks and don't infect documents, except in the case of Word macro viruses, which infect only documents and templates written in Word 6.0 or higher. They don't infect compressed files either. However, applications within a compressed file could have been infected before they were compressed. Viruses also don't infect computer hardware, such as monitors or computer chips; they only infect software.
In addition, Macintosh viruses don't infect DOS-based computer software and vice versa. For example, the infamous Michelangelo virus does not infect Macintosh applications. Again, exceptions to this rule are the Word and Excel macro viruses, which infect spreadsheets, documents and templates, which can be opened by either Windows or Macintosh computers.
Finally, viruses don't necessarily let you know that they are there - even after they do something destructive.
Types of Computer Viruses
Nowadays number of viruses is about 55000. It increases constantly. New unknown types of viruses appear. To classify them becomes more and more difficult. In common they can be divided by three basic signs: a place of situating, used operation system and work algorithms. For example according these three classifications virus Chernobyl can be classified as file infector and resident Windows virus. Further it will be explained what it means.
A place of existence
File Infectors
These are viruses that attach themselves to (or replace).COM and.EXE files, although in some cases they can infect files with extensions.SYS,.DRV,.BIN,.OVL and.OVY. With this type of virus, uninfected programs usually become infected when they are executed with the virus in memory. In other cases they are infected when they are opened (such as using the DOS DIR command) or the virus simply infects all of the files in the directory is run from (a direct infector).
There are three groups of file infectors.
Viruses of the first group are called overwriting viruses because they overwrite their code into infected file erasing contents. But these viruses are primitive and they can be found very quickly.
Other groupis called parasitic or cavity viruses. Infected file is capable of work fully or partly but contents of last one are changed. Viruses can copy itself into begin, middle or end of a file. They record their code in data known not to be used.
Third groupis called companion viruses. They don’t change files. They make double of infected file so when infected file is being started a double file becomes managing, it means virus. For example companion viruses working with DOS use that DOS firstly runs COM. file and after if this file is not found runs EXE. file. Viruses make double file with a same name and with extension COM and copies itself in this file. During start of infected file DOS runs a COM. file with a virus firstly and then a virus starts an EXE. file.
Sometime companion viruses rename file will be infected and record their code in a double file with old name. For example the file XCOPY.EXE is renamed into XCOPY.EXD and virus record itself in file XCOPY.EXE. When this file is started computer runs a virus code firstly and after virus starts original XCOPY, saved as XCOPY.EXD. Viruses like this were found not only in DOS. They were found in Windows and OS/2.
It is not only one way to make double files. For example there is subgroup of companion viruses called path-companion viruses. They use special feature of DOS - PATH: hierarchical record of file location. Virus copies itself in file with the same name but situated one level higher. In this case DOS will find file with virus.
Boot viruses
Boot Sector Infectors
Every logical drive, both hard disk and floppy, contains a boot sector. This is true even of disks that are not bootable. This boot sector contains specific information relating to the formatting of the disk, the data stored there and also contains a small program called the boot program (which loads the DOS system files). The boot program displays the familiar "Non-system Disk or Disk Error" message if the DOS system files are not present. It is also the program that gets infected by viruses. You get a boot sector virus by leaving an infected diskette in a drive and rebooting the machine. When the boot sector program is read and executed, the virus goes into memory and infects your hard drive. Remember, because every disk has a boot sector, it is possible (and common) to infect a machine from a data disk. NOTE: Both floppy diskettes and hard drives contain boot sectors.
|
|
|
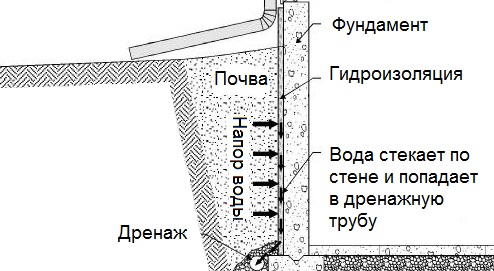
Общие условия выбора системы дренажа: Система дренажа выбирается в зависимости от характера защищаемого...
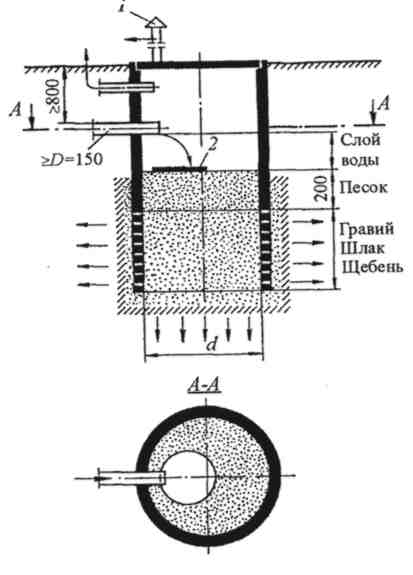
Индивидуальные очистные сооружения: К классу индивидуальных очистных сооружений относят сооружения, пропускная способность которых...

История создания датчика движения: Первый прибор для обнаружения движения был изобретен немецким физиком Генрихом Герцем...

Индивидуальные и групповые автопоилки: для животных. Схемы и конструкции...
© cyberpedia.su 2017-2024 - Не является автором материалов. Исключительное право сохранено за автором текста.
Если вы не хотите, чтобы данный материал был у нас на сайте, перейдите по ссылке: Нарушение авторских прав. Мы поможем в написании вашей работы!