

Таксономические единицы (категории) растений: Каждая система классификации состоит из определённых соподчиненных друг другу...
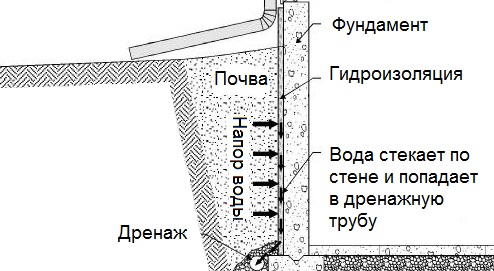
Общие условия выбора системы дренажа: Система дренажа выбирается в зависимости от характера защищаемого...

Таксономические единицы (категории) растений: Каждая система классификации состоит из определённых соподчиненных друг другу...

Общие условия выбора системы дренажа: Система дренажа выбирается в зависимости от характера защищаемого...
Топ:
История развития методов оптимизации: теорема Куна-Таккера, метод Лагранжа, роль выпуклости в оптимизации...
Оснащения врачебно-сестринской бригады.
Генеалогическое древо Султанов Османской империи: Османские правители, вначале, будучи еще бейлербеями Анатолии, женились на дочерях византийских императоров...
Интересное:
Средства для ингаляционного наркоза: Наркоз наступает в результате вдыхания (ингаляции) средств, которое осуществляют или с помощью маски...
Как мы говорим и как мы слушаем: общение можно сравнить с огромным зонтиком, под которым скрыто все...
Искусственное повышение поверхности территории: Варианты искусственного повышения поверхности территории необходимо выбирать на основе анализа следующих характеристик защищаемой территории...
Дисциплины:
|
из
5.00
|
Заказать работу |
|
|
|
|
Presentation requirements: format – MS Power Point, number of slides from 10 to 15, animation (optional, but recommended), presentation plan from 5 to 10 points, performance time from 5 to 7 minutes.
UNIT 6
Ex.1. Read and translate the text:
Cryptography
Cryptography or cryptology (from Greek κρυπτός kryptós, "hidden, secret"; and γράφειν graphein, "writing", or -λογία -logia, "study", respectively) is the practice and study of techniques for secure communication in the presence of third party called adversary1. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages; various aspects in information security such as data confidentiality, data integrity, authentication2, and non-repudiation3 are central to modern science of cryptography. It exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards4, computer passwords, and electronic commerce.
Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense. The originator of an encrypted message (Alice) shared the decoding technique needed to recover the original information only with intended recipients (Bob), thereby precluding unwanted persons (Eve) from doing the same. The cryptography literature often uses Alice ("A") for the sender, Bob ("B") for the intended recipient, and Eve ("eavesdropper") for the adversary. Since the development of rotor cipher machines in World War I and the advent of computers in World War II, the methods used to carry out cryptology have become increasingly complex and its application more widespread.
Cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible5 to do so by any known practical means. These schemes are therefore termed computationally secure; theoretical advances, e.g., improvements in integer factorization algorithms, and faster computing technology require these solutions to be continually adapted. There exist information-theoretically secure schemes that provably cannot be broken even with unlimited computing power, but these schemes are more difficult to implement than the best theoretically breakable6 but computationally secure mechanisms.
The growth of cryptographic technology has raised a number of legal issues in the information age. Cryptography's potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and copyright infringement7 of digital media.
|
|
Until modern times, cryptography referred almost exclusively to encryption, which is the process of converting ordinary information (called plaintext) into unintelligible text8 (called cipher text). Decryption is the reverse, in other words, moving from the unintelligible cipher text back to plaintext. A cipher (or cypher) is a pair of algorithms that create the encryption and the reversing decryption. The detailed operation of a cipher is controlled both by the algorithm and in each instance by a "key". The key is a secret (ideally known only to the communicants), usually a short string of characters9, which is needed to decrypt the cipher text. Formally, a “cryptosystem” is the ordered list of elements of finite possible plaintexts, finite possible cipher texts, finite possible keys, and the encryption and decryption algorithms which correspond to10 each key. Keys are important both formally and in actual practice, as ciphers without variable keys can be trivially broken with only the knowledge of the cipher used and are therefore useless (or even counter-productive11) for most purposes. Historically, ciphers were often used directly for encryption or decryption without additional procedures such as authentication or integrity checks.
There are two kinds of cryptosystems: symmetric and asymmetric. In symmetric systems the same key (the secret key) is used to encrypt and decrypt a message. Data manipulation in symmetric systems is faster than asymmetric systems as they generally use shorter key lengths. Asymmetric systems use a public key to encrypt a message and a private key to decrypt it. Use of asymmetric systems enhances12 the security of communication. Examples of asymmetric systems include RSA (Rivest-Shamir-Adleman13), and ECC (Elliptic Curve Cryptography14). Symmetric models include the commonly used AES (Advanced Encryption Standard15) which replaced the older DES (Data Encryption Standard16).
In colloquial use, the term "code" is often used to mean any method of encryption or concealment of meaning. However, in cryptography, code has a more specific meaning. It means the replacement of a unit of plaintext (i.e. a meaningful word or phrase) with a code word (for example, "wallaby" replaces "attack at dawn").
Cryptanalysis is the term used for the study of methods for obtaining the meaning of encrypted information without access to the key normally required to do so; i.e., it is the study of how to crack encryption algorithms or their implementations17.
Some use the terms cryptography and cryptology interchangeably in English, while others (including US military practice generally) use cryptography to refer specifically to the use and practice of cryptographic techniques and cryptology to refer to the combined study of cryptography and cryptanalysis. English is more flexible than several other languages in which cryptology (done by cryptologists) is always used in the second sense above. RFC 282818 advises that steganography19 is sometimes included in cryptology.
The study of characteristics of languages that have some application in cryptography or cryptology (e.g. frequency data, letter combinations, universal patterns, etc.) is called cryptolinguistics20.
|
|
NOTES
1. adversary – противник, оппонент, враг
2. authentication – аутентификация
3. non-repudiation – безотказность
4. ATM cards (Automatic Teller Machine card) – пластиковая банковская карта для банкомата
5. infeasible – невыполнимый, неосуществимый
6. theoretically breakable – теоретически подверженный взлому
7. copyright infringement – нарушение авторских прав
8. unintelligible text – непонятный (неразборчивый) текст
9. string of characters– строка символов
10. correspond to - соотноситься
11. counter-productive - контрпродуктивный
12.enhance – усиливать, повышать
13.RSA (Rivest-Shamir-Adleman) – фамилии ученых, создавших систему криптографии.
14.ECC (Elliptic Curve Cryptography) – криптография на эллиптических кривых
15. AES (Advanced Encryption Standard) – продвинутый стандарт шифрования
16. DES (Data Encryption Standard) – стандарт шифрования данных
17. implementation – осуществление, реализация, применение
18. RFC 2828 (Request For Comments) Глоссарий терминов интернет безопасности
19. steganography – стеганография
20. cryptolinguistics – криптолингвистика
|
|
|

Общие условия выбора системы дренажа: Система дренажа выбирается в зависимости от характера защищаемого...
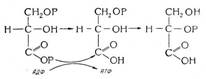
Биохимия спиртового брожения: Основу технологии получения пива составляет спиртовое брожение, - при котором сахар превращается...
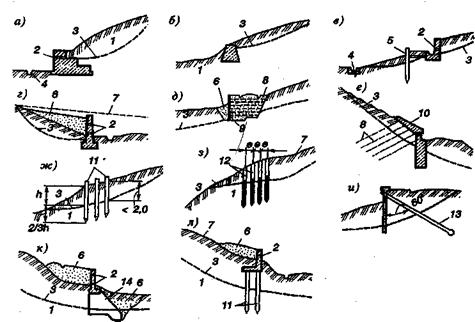
Механическое удерживание земляных масс: Механическое удерживание земляных масс на склоне обеспечивают контрфорсными сооружениями различных конструкций...
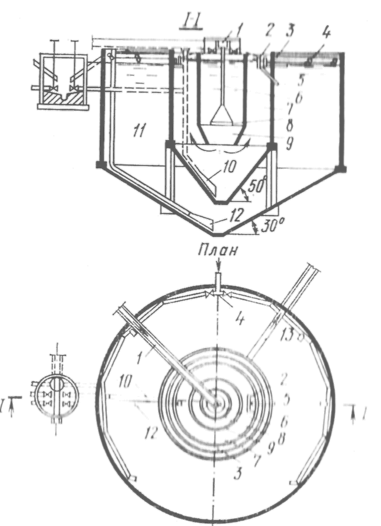
Типы сооружений для обработки осадков: Септиками называются сооружения, в которых одновременно происходят осветление сточной жидкости...
© cyberpedia.su 2017-2024 - Не является автором материалов. Исключительное право сохранено за автором текста.
Если вы не хотите, чтобы данный материал был у нас на сайте, перейдите по ссылке: Нарушение авторских прав. Мы поможем в написании вашей работы!