
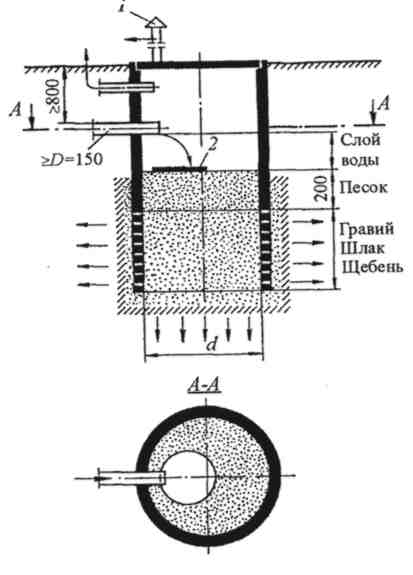
Индивидуальные очистные сооружения: К классу индивидуальных очистных сооружений относят сооружения, пропускная способность которых...
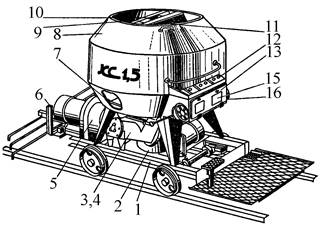
Кормораздатчик мобильный электрифицированный: схема и процесс работы устройства...

Индивидуальные очистные сооружения: К классу индивидуальных очистных сооружений относят сооружения, пропускная способность которых...

Кормораздатчик мобильный электрифицированный: схема и процесс работы устройства...
Топ:
Характеристика АТП и сварочно-жестяницкого участка: Транспорт в настоящее время является одной из важнейших отраслей народного...
Генеалогическое древо Султанов Османской империи: Османские правители, вначале, будучи еще бейлербеями Анатолии, женились на дочерях византийских императоров...
Интересное:
Национальное богатство страны и его составляющие: для оценки элементов национального богатства используются...
Искусственное повышение поверхности территории: Варианты искусственного повышения поверхности территории необходимо выбирать на основе анализа следующих характеристик защищаемой территории...
Мероприятия для защиты от морозного пучения грунтов: Инженерная защита от морозного (криогенного) пучения грунтов необходима для легких малоэтажных зданий и других сооружений...
Дисциплины:
|
из
5.00
|
Заказать работу |
|
|
|
|
24. Find the correct translation:
| 1. cover letter | А. коммерческое, рекламное письмо |
| 2. inquiry letter | B. разрешающее письмо |
| 3. sales letter | C. письменный заказ |
| 4. follow-up letter | D. рекламация |
| 5. complaint letter | E. письмо-запрос |
| 6.letter of resignation | F. письмо-поправка |
| 7.order letter | G. заявление об увольнении |
| 8.adjustment letter | H. письмо-напоминание |
| 9.acknowledgment letter | I. сопроводительное письмо |
25. Read and d efine the types of business letters:
1
|
A Letter of Application b Memo
C CV d Letter of complaint
| Dear Akram, Thank you for your fax. I was sorry to hear that you’ve had some problems with the WR 458. We do all we can to make sure that our products leave our factory in perfect condition, but unfortunately sometimes a bad one does slip through. If you can arrange for it to be returned to me, I’ll let you have a replacement by return. Hoping that you are keeping well, Regards Tony Anthony Hopkins. |
A Contract b Memo
C CV d Letter of apology
| In the winter issue of Multimedia News we read that your company sells language laboratories. Our school needs a new language laboratory and we are looking for the best equipment. Could you please send us information on your laboratories and include a price list and ordering information. Thank you for your assistance. I look forward to hearing from you. |
A Letter of enquiry/request b CV
C Contract d Letter of complaint
| Dear Sir or Madam: In the April 4, 2006 Boston Daily News I read about your new camera the XL-Lite. Since I am a photographer with Bay State Magazine, it is important that I know about new cameras. Would you please send me information on the camera? I would like to know when the camera will be available and how much it will cost. Thank you for your attention. |
A CV b Letter of enquiry/request
C Memo d Letter of complaint
| I am writing in connection with the above invoice for an MX3 Facsimile machine. We received this machine yesterday. Unfortunately, the power cable is missing. We would be grateful if you could send us one as soon as possible. |
A Letter of complaint b CV
|
|
C Letter of apology d Contract
| Responsible for training and mentoring system technicians and system designs. Also responsible for ensuring that delegated tasks are done accurately, on-time, billed within budget, and performed within the scope of the contract. Must also oversee that safety standards are adhered to. |
A Letter of inquiry b Contract
C Job advertisement d Memo
| Tony Spencer keeps parking his car in front of the main door. I have told him before that this place is reserved for the Managing Director. Can you tell him again? |
A Contract b CV
C Memo d Letter of Application
| I have enclosed my resume, and I would like to schedule an interview. I will call you early next week. I look forward to meeting you. |
A Letter of Application b Memo
C CV d Letter of complaint
| I was very sorry to hear about your problems with the new medical equipment. I have investigated the complaint and I regret to tell you that the problem is the result of faulty operation. I enclose a copy of the inspector’s report with this letter. If you require us to repair the machine, please contact me at the number above. |
A Contract b Letter of apology
C CV d Letter of Application
| Newell Ltd., hereinafter referred to as the Sellers on the one hand and Messrs. RusImport, hereinafter referred to as the Buyers, on the other hand, have concluded this Contract, whereby the Sellers sold and the Buyers bought on the terms and conditions stated herein, subject to the Standard Conditions of Sale attached to this Contract and forming an integral part thereof 25 SECURITY DEVICES … |
A Contract b Memo
C CV d Letter of enquiry/request
26. Write a sales letter to persuade your group mates to buy a new app/ gadget.
27. Write an order letter to purchase an app/ a gadget.
28. Your new gadget doesn’t function properly. Find a template and write a complaint letter.
UNIT 12
COMPUTER SECURITY, MALWARE & ANTIVIRUS DETECTION
1. Work with a group-mate to discuss the following:
1. Is cyber space secure now? Is cyber security an essential issue?
2. Have you ever been a victim of a cybercrime?
3. Will it be more or less secure in the future? Why?
4. Is it easy to steal sensitive information?
5. What is the difference between white hat and black hat hackers?
Part I. TEXT
1. Here are the words and word combinations you have to learn. Rewrite them and find their meaning using online translator (www.lingvolive.com, www.multitran.ru):
Protection, computer security, security measure, advanced security technique, valuable or sensitive equipment, threat, theft of data, fraud, invasion of privacy, means of protecting, irresponsible behavior, to assign an individual password, to encrypt, a singular encryption key, to decipher, proliferation, to diminish a threat, a refinement.
2. Read and compare the terms “information security” and “computer/cyber security”. Which term is broader?
Information being an asset to all individuals and businesses, information security is designed to protect information from those with malicious intentions. Information you are trying to keep safe is your “data,” and this refers to any form of data, whether it is electronic or on paper.Computer security is the protection of information in its electronic form: computing systems and the data that they store or access.
|
|
3. Confidentiality, integrity and availability are sometimes referred to as the CIA Triad of information security. Match the components of CIA Triad of information security with their examples (2 for each component):
Components:
1. Confidentiality is referred to as protecting information from being disclosed to unauthorized parties. 2. Integrity can be defined as protecting information from being changed by unauthorized parties. 3. Availability is the availability of information to authorized parties only when requested.
Examples:
A. When submitted to a website, your personal data should not be altered in any way during data transmission, or by the website company. B. You should be able to access and check your personal data kept on a website at any time. C. When submitted to a website, your personal data should only be used or accessed exclusively by designated staff in that company for the agreed purposes. No one else should be allowed to use your data for illegal purposes, or view the data out of curiosity. D. Clients should be able to access any of their data kept by the company when they request it. E. Sensitive information, such as sales figures or client data, should only be accessed by authorized persons such as senior management and the sales team, and not other operations or departments. F. Important documents or figures should not be changed or altered by unauthorized persons without prior notice.
4. Read and translate the text:
TEXT 1. Computer security
The protection of information and computer systems from harm, theft, and unauthorized use is referred to as computer security. Computer hardware is typically protected by the same means used to protect other valuable or sensitive equipment, namely, serial numbers, doors and locks, and alarms. The protection of information and system access, on the other hand, is achieved through other tactics, some of them being quite complex.
The security precautions related to computer information and access address four major threats: (1) theft of data, such as that of military secrets from government computers; (2) vandalism, including the destruction of data by a computer virus; (3) fraud, such as employees at a bank channeling funds into their own accounts; and (4) invasion of privacy, such as the illegal accessing of protected personal financial or medical data from a large database.
The most basic means of protecting a computer system against theft, vandalism, invasion of privacy, and other irresponsible behaviors is to electronically track and record the access to and activities of the various users of a computer system. This is commonly done by assigning an individual password to each person who has access to a system. The computer system itself can then automatically track the use of these passwords, recording such data as which files were accessed under particular passwords and so on. Another security measure is to store a system’s data on a separate device, or medium, such as magnetic tape or disks, that is normally inaccessible through the computer system. Finally, data is often encrypted so that it can be deciphered only by holders of a singular encryption key.
Computer security has become increasingly important since the late 1960s, when modems (devices that allow computers to communicate over telephone lines) were introduced. The proliferation of personal computers in the 1980s compounded the problem because they enabled hackers (irresponsible computer files) to illegally access major computer systems from the privacy of their homes. The development of advanced security techniques continues to diminish such threats, though concurrent refinements in the methods of computer crime pose ongoing hazards.
(From: https://www.britannica.com/technology/computer-security)
5. True, false or no information? Find the sentences in the text that support your point of view.
|
|
1. The destruction of data by a computer virus is called vandalism.
2. Sensitive information, such as sales figures or client data, should only be accessed by authorized persons.
3. Viruses can be used to harm host computers and networks.
4. Computer security has become increasingly important since the late 1960s with the proliferation of personal computers.
5. Serial numbers, doors and locks are typically used to protect computer hardware.
6. Fraud is the illegal accessing of protected personal financial or medical data from a large database.
7. An individual password is used as the most basic means of protecting a computer system.
6. Ask questions about means of computer security using the following patterns:
a. I would like to know, if /whether …
b. Can you tell me what/which/when/why …?
c. Does anybody know what/which/when/why …?
d. Are you sure that …?
e. Do you agree that …?
7. Prepare a short summary of the text “ Computer security” using the expressions (See Appendix II for annotation details).
8. Malware is a broad term that refers to a variety of malicious programs. What types of such programs do you know? What harm can malware do to your computer?
9. Here are more words to be learned:
to compromise computer functions, to steal data, to bypass access controls, to cause harm to, remote access, worm, adware, spyware, Trojan horse, bot, bug, ransomware, rootkit, cross-site scripting vulnerability, to consume bandwidth, to overload web servers, payload, to distinguish, ability to self-replicate, to deliver advertisements, a revenue generating tool, to come bundled with, to spy on user activity, to collect keystrokes, data harvesting, to disguise, DDoS attack, flaw, to hold a computer system captive, to restrict, to hide, suspicious
10. Read the text and speak about the types of malware.
TEXT 2. What is Malware?
Malware is short for mal icious soft ware, meaning software that can be used to compromise computer functions, steal data, bypass access controls, or otherwise cause harm to the host computer. The text will define several of the most common types of malware: viruses, worms, adware, spyware, Trojan horses, bots, bugs, ransomware and rootkits.
Computer Virus
A virus is a form of malware that is capable of copying itself and spreading to other computers. Viruses often spread to other computers by attaching themselves to various programs and executing code when a user launches one of those infected programs. Viruses can also spread through script files, documents, and cross-site scripting vulnerabilities in web apps. Viruses can be used to steal information, harm host computers and networks, create botnets, steal money, render advertisements, and more.
Worm
Computer worms are among the most common types of malware. They spread over computer networks by exploiting operating system vulnerabilities. Worms typically cause harm to their host networks by consuming bandwidth and overloading web servers. Computer worms can also contain “payloads” that damage host computers. Payloads are pieces of code written to perform actions on affected computers beyond simply spreading the worm. Payloads are commonly designed to steal data, delete files, or create botnets. Computer worms can be classified as a type of computer virus, but there are several characteristics that distinguish computer worms from regular viruses. A major difference is that computer worms have the ability to self-replicate and spread independently while viruses rely on human activity to spread (running a program, opening a file, etc). Worms often spread by sending mass emails with infected attachments to users’ contacts.
|
|
Adware
Adware (short for advertising-supported software) is a type of malware that automatically delivers advertisements. Common examples of adware include pop-up ads on websites and advertisements that are displayed by software. Software and applications usually offer “free” versions that come bundled with adware. Most adware is sponsored or authored by advertisers and serves as a revenue generating tool. While some adware is solely designed to deliver advertisements, it is not uncommon for adware to come bundled with spyware that is capable of tracking user activity and stealing information. Due to the added capabilities of spyware, adware/spyware bundles are significantly more dangerous than adware on its own.
Spyware
Spyware is a type of malware that functions by spying on user activity without their knowledge. These spying capabilities can include activity monitoring, collecting keystrokes, data harvesting (account information, logins, financial data), and more. Spyware often has additional capabilities as well, ranging from modifying security settings of software or browsers to interfering with network connections. Spyware spreads by exploiting software vulnerabilities, bundling itself with legitimate software, or in Trojans.
Trojan horse
A Trojan horse, commonly known as a “Trojan,” is a type of malware that disguises itself as a normal file or program to trick users into downloading and installing malware. A Trojan can give a malicious party remote access to an infected computer. Once an attacker has access to an infected computer, it is possible for the attacker to steal data (logins, financial data, electronic money), install more malware, modify files, monitor user activity (screen watching, keylogging, etc), use the computer in botnets, and anonymize internet activity by the attacker.
Bot
Bots are software programs created to automatically perform specific operations. While some bots are created for relatively harmless purposes (video gaming, internet auctions, online contests, etc), it is becoming increasingly common to see bots being used maliciously. Bots can be used in botnets (collections of computers to be controlled by third parties) for DDoS attacks, as spam bots that render advertisements on websites, as web spiders that scrape server data, and for distributing malware disguised as popular search items on download sites. Websites can guard against bots with CAPTCHA tests that verify users as human.
Bug
In the context of software, a bug is a flaw producing an undesired outcome. These flaws are usually the result of human error and typically exist in the source code or compilers of a program. Minor bugs only slightly affect a program’s behavior and as a result can go for long periods of time before being discovered. More significant bugs can cause crashing or freezing. Security bugs are the most severe type of bugs and can allow attackers to bypass user authentication, override access privileges, or steal data. Bugs can be prevented with developer education, quality control, and code analysis tools.
Ransomware
Ransomware is a form of malware that essentially holds a computer system captive while demanding a ransom. The malware restricts user access to the computer either by encrypting files on the hard drive or locking down the system and displaying messages that are intended to force the user to pay the malware creator to remove the restrictions and regain access to their computer. Ransomware typically spreads like a normal computer worm ending up on a computer via a downloaded file or through some other vulnerability in a network service.
Rootkit
A rootkit is a type of malicious software designed to remotely access or control a computer without being detected by users or security programs. Once a rootkit has been installed it is possible for the malicious party behind the rootkit to remotely execute files, access/steal information, modify system configurations, alter software (especially any security software that could detect the rootkit), install concealed malware, or control the computer as part of a botnet. Rootkit prevention, detection, and removal can be difficult due to their stealthy operation. Because a rootkit continually hides its presence, typical security products are not effective in detecting and removing rootkits. As a result, rootkit detection relies on manual methods such as monitoring computer behavior for irregular activity, signature scanning, and storage dump analysis. Organizations and users can protect themselves from rootkits by regularly patching vulnerabilities in software, applications, and operating systems, updating virus definitions, avoiding suspicious downloads, and performing static analysis scans.
|
|
Malware Symptoms
While the types of malware differ greatly in how they spread and infect computers, they all can produce similar symptoms. Computers that are infected with malware can exhibit any of the following symptoms:
· Increased CPU usage
· Slow computer or web browser speeds
· Problems connecting to networks
· Freezing or crashing
· Modified or deleted files
· Appearance of strange files, programs, or desktop icons
· Programs running, turning off, or reconfiguring themselves (malware will often reconfigure or turn off antivirus and firewall programs)
· Strange computer behavior
· Emails/messages being sent automatically and without user’s knowledge (a friend receives a strange email from you that you did not send).
11. True, false or no information? Find the sentences in the text that support your point of view.
1. Adware/ spyware bundles are significantly less dangerous than adware on its own.
2. Minor bugs are difficult to discover.
3. Ransomware is intended to force the user to pay the malware creator to remove the restrictions and regain access to their computer.
4. DDoS attacks overwhelm servers with requests until they are forced offline.
5. Computer viruses have the ability to self-replicate and spread independently while worms rely on human activity to spread.
6. Originally, bots aren’t harmful because they are created for video gaming, internet auctions, online translation etc.
7. Spyware is capable of stealing sensitive information.
8. Appearance of strange files and programs means that the computer is infected.
12. Ask questions about the types of malware using the following patterns:
a. I would like to know, if /whether …
b. Can you tell me what/which/how/why …?
c. Does anybody know what/which/how/why …?
d. Are you sure that …?
e. Do you agree that …?
13. Give a summary of the text “What is Malware?” using the expressions (See Appendix II for annotation details).
14. Read the text to learn about computer and network protection:
|
|
|
Наброски и зарисовки растений, плодов, цветов: Освоить конструктивное построение структуры дерева через зарисовки отдельных деревьев, группы деревьев...
Адаптации растений и животных к жизни в горах: Большое значение для жизни организмов в горах имеют степень расчленения, крутизна и экспозиционные различия склонов...
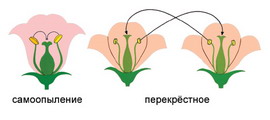
Семя – орган полового размножения и расселения растений: наружи у семян имеется плотный покров – кожура...

Археология об основании Рима: Новые раскопки проясняют и такой острый дискуссионный вопрос, как дата самого возникновения Рима...
© cyberpedia.su 2017-2024 - Не является автором материалов. Исключительное право сохранено за автором текста.
Если вы не хотите, чтобы данный материал был у нас на сайте, перейдите по ссылке: Нарушение авторских прав. Мы поможем в написании вашей работы!